The Company established an Information and Cyber Security Office on September 1, 2022, with one information security officer and one dedicated information security personnel. To effectively promote the implementation and operation of the company's Information Security Management System (ISMS), the Information and Cyber Security Management Committee was established on December 18, 2024, with the General Manager serving as the convener. A deputy convener and an executive secretary were appointed to coordinate the various tasks of the Information and Cyber Security Management Committee. Information security management representatives from the management levels of various business divisions and functional units are responsible for assisting in promoting and supervising the information security work of each unit. An Information Security Working Group was set up, divided into the following subgroups based on responsibilities: (1) Incident Response Team, (2) Information Asset Risk Management Team, (3) Document Management Team, and (4) Audit Team. Regarding the implementation and operation of the Company's Information Security Management System (ISMS), the system was officially announced in February 2025. The verification team from BSI Taiwan completed the two-phase verification in April 2025. After final confirmation by BSI Taiwan and headquarters, the ISO 27001:2022 certificate will be issued.
Information and Cyber Security Risk Management Framework
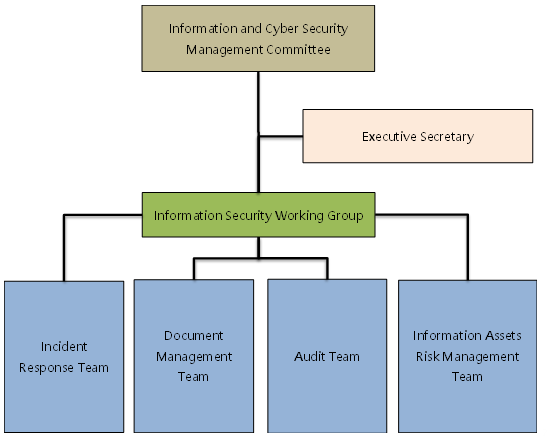
Responsibilities of the Information and Cyber Security Management Committee:
- Review the objectives and scope of the Information Security Management System.
- Review the implementation and effectiveness of information security management-related operations and improvements.
- Review information security-related policies and regulations, and coordinate the allocation and use of resources.
- Supervise the conduct of business continuity drills.
- Review the resources required for the implementation of corrective measures, including manpower, time, and budget.
- Review the effectiveness of corrective measures.
- Hold at least one management review meeting annually, with the option to convene additional meetings as necessary.
Information and Cyber Security Policy
In alignment with the core business characteristics of the Company, the Policy establishes a framework to protect the rights and interests of the Company and its stakeholders. (including but not limited to employees, customers, vendors/upstream suppliers, shareholders, investors, financial/securities institutions, non-vendor suppliers, government/competent authorities and society). All employees and the Company are collectively responsible for fostering a safe information and communication environment, enabling information security to be embedded into its corporate culture. The Company will implement a tailored-information security policy to clearly define security objectives and establish compliance requirements which shall be consistently upheld. For detailed information, please refer to the "Information and Cyber Security Policy" published on the Company's official website (Approved by the Board of Directors on January 13, 2025).
Objectives and Guidelines
- Each business unit of the Company shall comply with the provisions of relevant government laws and regulations (such as the Patent Act, the Copyright Act, the Personal Data Protection Act, and the Enforcement Rules of the Personal Data Protection Act) when conducting business and operations.
- The Information and Cyber Security Management Committee has been established and shall be responsible for the establishment and implementation of the Company's information security management system.
- The Company shall establish an organizational panorama evaluation mechanism to define the information security policy and the scope of implementation of the information security management system. The Committee/Company shall understand the needs and expectations of the stakeholders organizational level of.
- Formulate guidelines on document control and management, and set the management principles for the formulation, revision, document coding, and issuance of documents related to the information security management system.
- Establish a management mechanism for information assets to coordinate the allocation and effective use of limited resources to solve key security issues
- Establish risk assessment management methods and identify the risks of various types of assets, so as to take appropriate risk treatment measures to control and mitigate risks to an acceptable level.
- Regularly implement business-related information security training, and advocate information security policies and the implementation of regulations
- Establish physical and environmental safety protection measures for the datacenters room, and regularly conduct relevant maintenance
- Clearly specify guidelines of the use rights of information systems, network services, and sensitive information, to prevent unauthorized access.
- Establish operational procedures for the acquisition, development and maintenance of information systems, with specific guidelines of the compliance of systems in development and outsourcing. An evaluation shall be conducted regarding information security-related issues prior to the establishment or launch of information systems or services to prevent situations that may endanger system security.
- Establish and implement internal audit activities for information security to ensure the implementation of the information security management system. Corrective measures shall take place for any outstanding matters.
- Establish an information security operation continuity plan and conduct actual drills to ensure the Company's operational continuity in the event of an emergency.
- All personnel of the Company are responsible for maintaining information security and shall understand and comply with the relevant information security guidelines and policies, and implement such guidelines in their job duties.
2024 Information Security Personnel Related Education Courses and Activities:
| Organizer | Name of Course/Activity | Date | Hours | Participant | Certificate |
|---|
| Taiwan Corporate Governance Association |
Board of Directors Information Security Governance Oversight Strategy |
2024/05/17 |
3 |
ICSO Manager |
Taiwan Corporate Governance Association Study certificate - TCGA11302370 |
| Chunghwa Telecom Co., Ltd. |
Personal Information Law Education and Training |
2024/09/12 |
3 |
ICSO Manager* |
N/A |
| Taiwan Academy of Banking and Finance |
Information Security Awareness Essential Knowledge and Responsibilities |
2024/12/03 |
2 |
ICSO Manager |
Taiwan Academy of Banking and Finance certificate - IS100100001640 |
| Taiwan Academy of Banking and Finance |
Information Security Incidents and Preventive Action |
2024/12/05 |
2.5 |
ICSO Manager |
Taiwan Academy of Banking and Finance certificate - IS100110001640 |
| Taiwan Academy of Banking and Finance |
Information Security Management and Control Guidelines for the Exchange-Listed & OTC-Listed Companies |
2024/12/06 |
1.5 |
ICSO Manager |
Taiwan Academy of Banking and Finance certificate - IS100120001641 |
| Yuan Ze University |
Computer Security Incident Response |
2024/10/17 |
3 |
ICSO Staff |
Yuan Ze University certificate - YZULE3700188 |
Note: Our company conducts "Information Security Education and Training" for all employees for 1 hour annually, and for information personnel for 3 hours annually.
- On September 12, 2024, we conducted a Personal Data Protection Act training session (3 hours/439 participants, including ICSO Manager).
- In 2024, there were a total of 16 meetings for the implementation of the Information Security Management System (ISMS).
Procedures of Information and Cyber Security Incident Notification
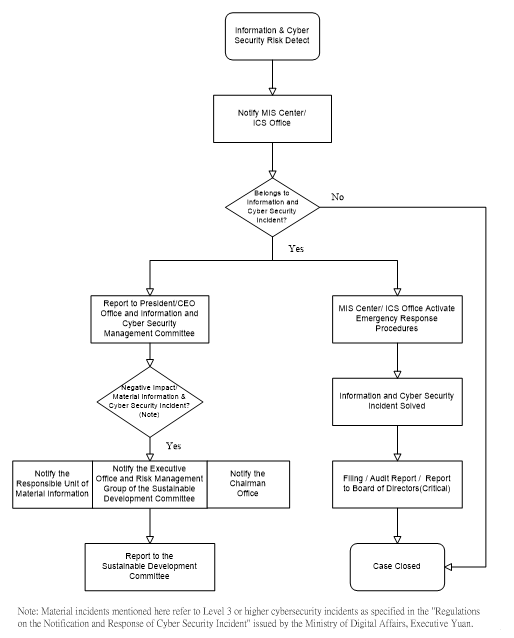
In 2023 and 2024, the Company had not suffered any losses or affected operations, goodwill, etc. due to the occurrence of material information and cyber security incidents.

